AWS Site-to-Site VPN and Peer to Peer connection on VPC
VPN connection refers to the connection between your VPCs and your own on premises network.
Key concepts of Site to Site VPN
VPN Connection: A secure connection between your on-premises network and your VPCs.
VPN tunnel: its a encrypted link where your data can pass from Customer network to or From AWS.
Each VPN can includes two VPN tunnels which can use for data high availability.
Customer gateway: This is AWS resource which will provide information about customer gateway device.
Customer gateway device: A physical device or software application on your side of the site-site VPN connection.
We can achieve site to site VPN connection by using the following interfaces.
- AWS Management console
- AWS CLI
- AWS SDK
- Query API
Limitation of site-Site VPN connection
- This won't support IPV6 traffic
- An AWS VPN connection that doesn't support mtu Path directory.
- Also Make sure that your VPC connection CIDR block should not overlap with on premises IPs.
How Site -Site VPN works
Virtual Private Gateway: We can create a virtual private gateway and attach to the VPC from amazon side from which you want to create a site-site VPN connection.
%3CmxGraphModel%3E%3Croot%3E%3CmxCell%20id%3D%220%22%2F%3E%3CmxCell%20id%3D%221%22%20parent%3D%220%22%2F%3E%3CmxCell%20id%3D%222%22%20value%3D%22%22%20style%3D%22rounded%3D1%3BwhiteSpace%3Dwrap%3Bhtml%3D1%3BfontFamily%3DTimes%20New%20Roman%3B%22%20vertex%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20x%3D%2240%22%20y%3D%2220%22%20width%3D%22780%22%20height%3D%22290%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3C%2Froot%3E%3C%2FmxGraphModel%3E
When you create Virtual private gateway , you have to specify ASN (Autonomous system number) for amazon side, if you don't specify ASN , the virtual private gateway is created with default ASN (64512).Once its created it won't be changed.
Transit gateway: This will provides the interconnection with virtual private clouds and on premises network.We can modify transit gateway with virtual private gateway.
VPC Endpoints
It enables to you to directly connect with your VPCs to AWS resourcces where in you no need to create /use the below
- NAT gateway/instance
- Internet gateway
- VPN connection
- Direct connect
Endpoints are horizontally scaled,highly available virtual devices.
Types of Endpoints
- Interface Endpoints:Is an elastic network interface which provides private IP address private IP address from the IP address range of your subnet that serves as an entry point for traffic destined to a supported service.Since it has private IP adderess and it is powered by privatelink of AWS which provides Private connection with your device from AWS.
- Gateway Endpoints: Is a gateway that you specify as a target for a route in your route table for traffic destined to a supported AWS service.
VPC Peer to Peer connection
This means providing connection between two VPCs either by using IPV4 or IPV6 address which are using the same network.
VPC peering can be between in your own VPCs or with another account VPC.
VPCs can be in different region.
To implement Peering connection , AWS uses the existing infrastructure , which does not uses neither NAT gateway or VPN connection .
There is no single point of failure or bottleneck with this feature.
- The owner of the requester VPC sends a request to the owner of the accepter VPC to create the VPC peering connection. The accepter VPC can be owned by you, or another AWS account, and cannot have a CIDR block that overlaps with the requester VPC's CIDR block.
- The owner of the accepter VPC accepts the VPC peering connection request to activate the VPC peering connection.
- To enable the flow of traffic between the VPCs using private IP addresses, the owner of each VPC in the VPC peering connection must manually add a route to one or more of their VPC route tables that points to the IP address range of the other VPC (the peer VPC).
- If required, update the security group rules that are associated with your instance to ensure that traffic to and from the peer VPC is not restricted. If both VPCs are in the same region, you can reference a security group from the peer VPC as a source or destination for ingress or egress rules in your security group rules.
- By default, if instances on either side of a VPC peering connection address each other using a public DNS hostname, the hostname resolves to the instance's public IP address. To change this behavior, enable DNS hostname resolution for your VPC connection. After enabling DNS hostname resolution, if instances on either side of the VPC peering connection address each other using a public DNS hostname, the hostname resolves to the private IP address of the instance.
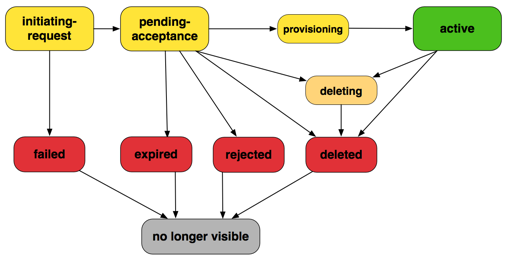
limitations of Peering connections:
- You cannot create a VPC peering connection between VPCs that have matching or overlapping IPv4 or IPv6 CIDR blocks.
- You have a quota on the number of active and pending VPC peering connections that you can have per VPC
- VPC peering does not support transitive peering relationships.
- You cannot have more than one VPC peering connection between the same two VPCs at the same time.
No comments:
Post a Comment